Detecting Node-Hopping Attackers: Correlating Traces and Logs at Sub-Second Speed
Sep 8, 2025

Introduction
Modern cyberattacks rarely stop at a single system. Once inside, attackers often move laterally, jumping between machines and services, in search of sensitive data or admin access. This tactic is known as node-hopping or lateral movement.
Detecting these attackers is not easy. Each step looks harmless in isolation. But when you connect logs and traces across systems, the pattern becomes clear. The key is doing it fast with real-time log correlation and sub-second detection speeds.
What Is Node-Hopping (Lateral Movement)?
Node-hopping, a form of lateral movement, happens when:
- An attacker compromises one machine (Node A).
- Steals user credentials or tokens.
- Uses them to log in to another system (Node B).
- Repeats the process until they reach sensitive servers or data.
In simple terms, it’s like a burglar sneaking room to room inside a building, rather than breaking directly into the vault.
Why Node-Hopping Attacks Are Hard to Detect
Lateral movement detection is difficult because attackers:
- Mimic normal activity. Logins, file access, or admin commands look legitimate on their own.
- Exploit log silos. Server logs, network logs, and cloud traces live in separate systems. Without centralized log correlation, the bigger picture is missed.
- Rely on delays. If your SIEM or monitoring tool processes logs in minutes or hours, attackers can move several hops before you even notice.
This is why real-time threat detection is critical.
How Real-Time Log and Trace Correlation Works
Logs record what happens inside each machine: logins, process starts, file access, and more. On their own, these entries can look normal. But when you correlate logs across multiple systems in real time, you start to see suspicious chains of activity that reveal lateral movement.
For example, you might find a pattern like:
- Node A → A user logs in.
- Node B → A remote connection happens.
- Node C → An admin command is executed.
Individually, none of these is alarming. Logins, remote connections, and admin commands all happen in normal operations. Together, they paint the picture of a node-hopping attacker.
Traces add another layer of visibility; many systems tag logs with session IDs or trace IDs. Traces essentially act as the thread that ties logs together into a clear attack path.
This makes it easier to follow an attacker’s path step by step, from one node to the next.. Without traces, you’d have to infer connections by timing, usernames, or IP addresses. With trace IDs, the link is explicit.
And if you correlate them (look at them together, in sequence, within a short time window), you realize this is suspicious:
- A user logged into one machine.
- Seconds later, that login was used to jump into another machine.
- Then an admin-level action took place on a third machine.
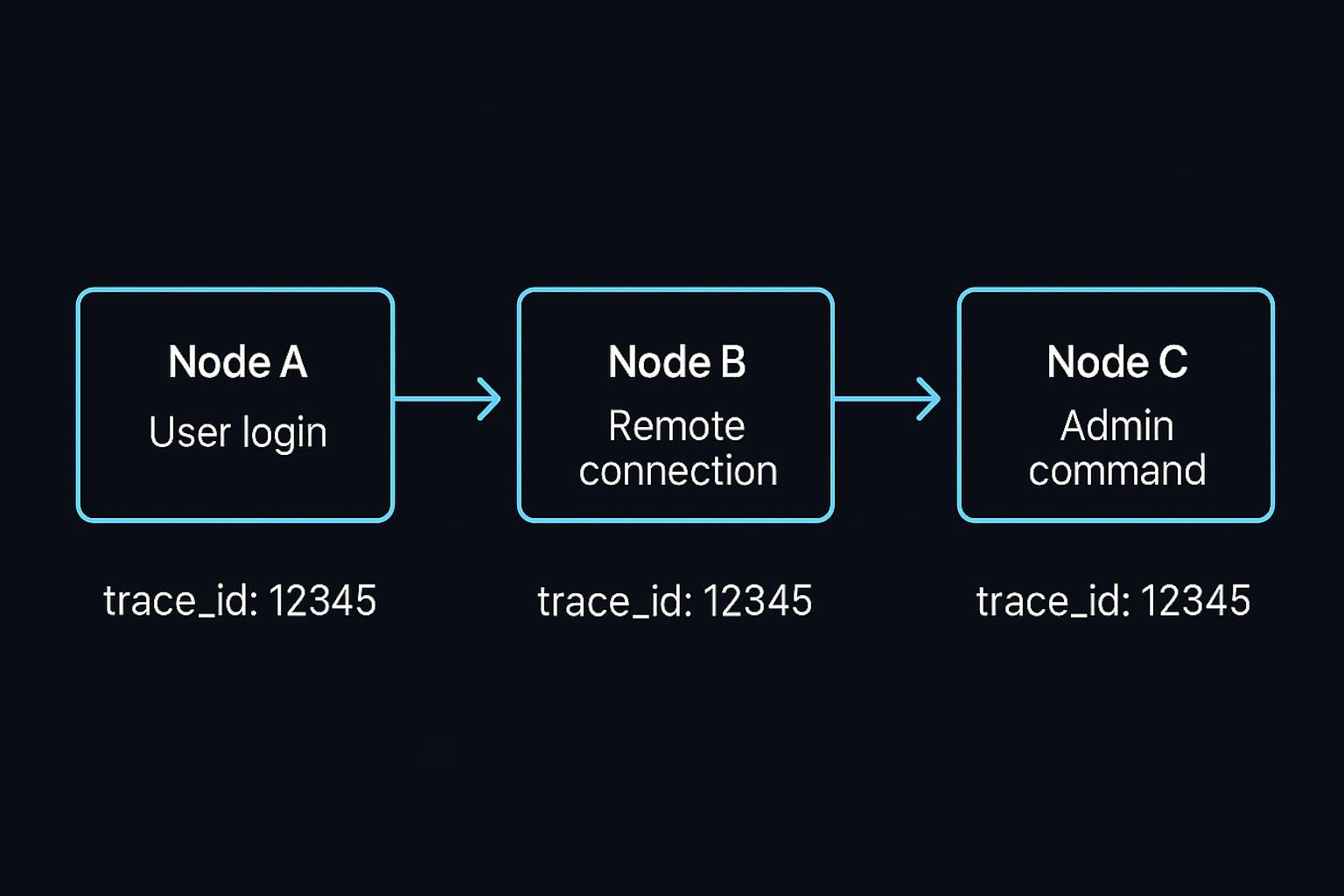
Logs are the raw events. But many systems also tag these logs with trace IDs (or session IDs).
- Think of a trace ID as a thread or breadcrumb trail that ties related events together across systems.
- If Node A and Node B both have logs carrying the same trace ID, you instantly know those actions are connected.
This isn’t an after-the-fact investigation; it’s lateral movement detection in real time, giving defenders the speed to contain threats before they spread.
Why Sub-Second Detection Matters
Now, let’s add speed into the picture. If your system can:
- Correlate these events in real time, and
- Spot when a suspicious chain is forming
…then you can catch the attacker while they’re still moving.
That’s the difference between:
- Batch analysis → you discover the attack hours later, when damage is already done.
- Sub-second correlation → You raise an alert the moment the sequence unfolds, giving your team a chance to respond immediately.
With logs + traces correlated in real time, you can:
- Spot attack chains instantly. Instead of seeing just “a login” or “a process,” you see the whole suspicious story.
- Build clear attack paths. Logs linked by trace IDs make it easy to visualize: Node A → Node B → Node C.
- Trigger alerts early. Instead of incident response being a postmortem exercise, you intervene while the attacker is active.

Why Speed and Visibility Matter
Speed and visibility are the foundations of effective threat detection:
- Lower MTTD (Mean Time to Detect). Sub-second log analysis shrinks detection times from hours to milliseconds.
- Faster incident response. Teams can disable accounts or isolate machines before attackers escalate privileges.
- End-to-end visibility. Correlating logs and traces across all systems (servers, networks, cloud) eliminates blind spots.
Attackers depend on slow, siloed systems. Real-time correlation turns the tables.
Tools for Real-Time Lateral Movement Detection
Different types of platforms support real-time log correlation and lateral movement detection:
- Modern SIEM platforms – Collect logs from across environments and apply correlation rules to detect suspicious sequences.
- Extended Detection and Response (XDR) solutions – Combine endpoint, network, and identity data for a unified view of attacker behavior.
- Distributed tracing and observability tools – Track activity across applications and services, linking traces with logs for richer context.
- Streaming analytics frameworks – Process logs and traces at scale in real time, enabling sub-second alerting.
Each of these plays a role in helping security teams gain speed and visibility, but they often come with trade-offs around cost, complexity, or data retention limits.
Conclusion
Node-hopping attackers thrive on blind spots and slow monitoring. Traditional methods miss the bigger picture because they analyze logs in isolation or too late.
The solution is real-time log and trace correlation at sub-second speed. By connecting events across systems instantly, you can expose lateral movement attacks in progress, not after the damage is done.
Speed plus visibility equals stronger defense. With the right tools and approach, defenders can catch node-hopping attackers in motion and shut them down before they reach critical targets.
At CtrlB, we believe, correlating logs and traces should not come at the cost of either speed or affordability. By pairing sub-second log search with trace-aware correlation directly from durable object storage, we help teams catch lateral movement even in historical data, without maintaining massive hot indexes or expensive SIEM stacks.